
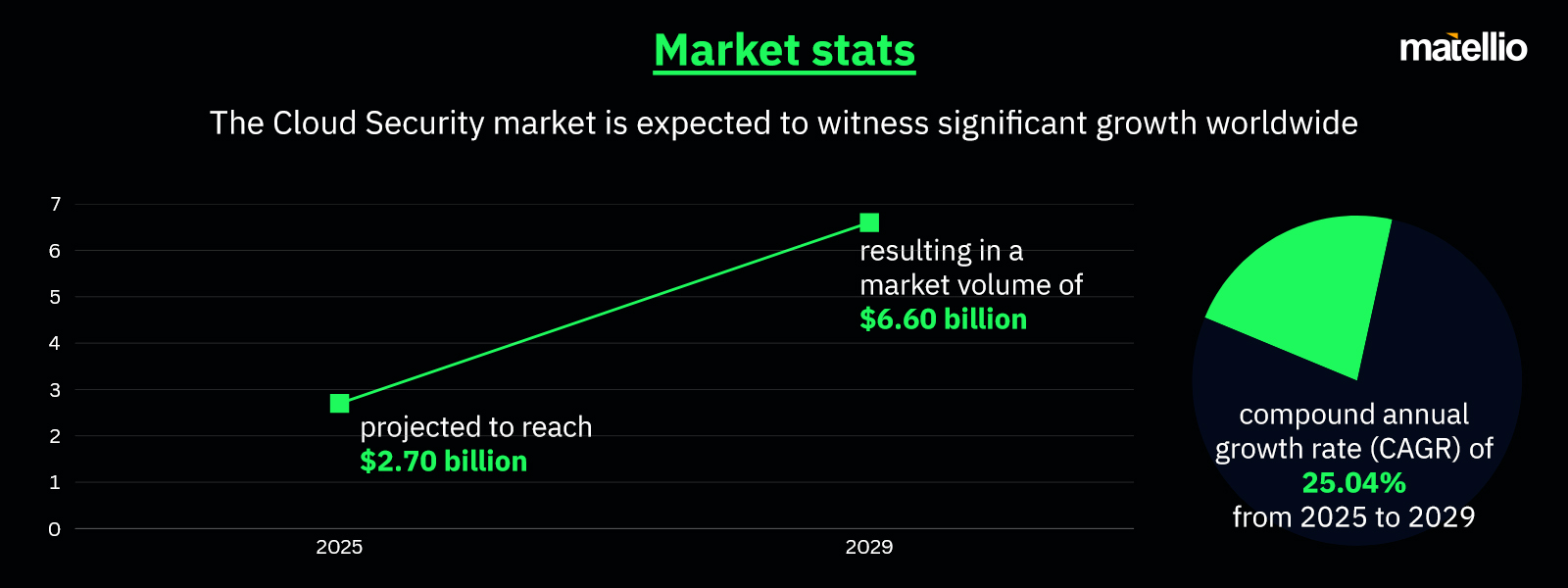
The adoption of cloud-based applications has revolutionized the way businesses operate, offering unparalleled flexibility, scalability, and cost efficiency. From managing critical workloads to enabling remote workforces, cloud applications have become indispensable across industries. However, this rapid adoption has also exposed organizations to a new wave of cybersecurity threats, underscoring the critical need for robust cloud application security measures.
Protecting sensitive data and ensuring uninterrupted business operations are at the core of maintaining trust and competitiveness in today’s digital landscape. This blog explores the fundamentals of cloud application security, its significance for businesses, effective strategies, enabling technologies, and the trends shaping its future.
What Is Cloud Application Security?
Cloud application security refers to the strategies, technologies, and practices designed to safeguard cloud-based applications from cyber threats, unauthorized access, and vulnerabilities. As organizations increasingly migrate to cloud environments, robust security becomes essential to ensure operational continuity, data privacy, and compliance with industry regulations. Cloud application security encompasses a holistic approach, combining proactive threat prevention, continuous monitoring, and reactive measures to maintain system integrity.
Key Components of Cloud Application Security
1. Access Management
Managing access is critical to ensuring that only authorized users interact with sensitive data and systems.
- Use multi-factor authentication (MFA) for enhanced access control.
- Implement user role management to grant access based on job requirements.
With cloud consulting services, businesses can streamline their access management policies, ensuring effective user control and minimizing unauthorized breaches.
2. Data Security
Protecting sensitive information is a cornerstone of cloud security.
- Encrypt data at rest and in transit to safeguard against interception.
- Implement secure key management protocols to protect encryption keys.
- Cloud data security best practices ensure that your information remains protected, maintaining customer trust and regulatory compliance.
3. Threat Detection
Proactive threat detection is vital in identifying and neutralizing risks before they escalate.
- Leverage AI-powered tools for anomaly detection and predictive analysis.
- Conduct real-time monitoring for immediate identification of suspicious activity.
By incorporating cloud security technologies, organizations can stay ahead of evolving threats.
4. Incident Response
Even the most secure systems can face breaches; effective incident response ensures damage control.
- Create pre-defined protocols for handling breaches swiftly and efficiently.
- Automate response mechanisms to isolate and mitigate threats immediately.
Application security in the cloud emphasizes readiness, ensuring quick recovery and minimal disruption.
5. Compliance and Governance
Staying compliant with regulations like GDPR, HIPAA, and PCI DSS is crucial for avoiding penalties.
- Regularly audit security policies to ensure adherence to industry standards.
- Use automated compliance tools for consistent tracking and reporting.
Cloud computing security compliance guarantees businesses remain aligned with regulatory frameworks, protecting their operations and reputation.
Traditional vs. Cloud-Native Security
- Traditional Security Models: Focus on perimeter-based defenses, such as firewalls, to secure on-premises systems. These approaches are less effective in modern, distributed environments where applications and data are accessed from multiple locations.
- Cloud-Native Security Models: Emphasize a zero-trust architecture where every access request is verified, regardless of its origin. Security is embedded within the cloud infrastructure, ensuring that data and applications are protected across distributed environments.
Cloud-native approaches are particularly effective in dealing with modern threats, as they are designed for the dynamic nature of cloud ecosystems.
Why It Matters
Cloud application security is more than a protective layer—it’s a business enabler. It ensures that organizations can leverage the scalability and flexibility of cloud platforms without compromising on security. From protecting sensitive customer data to meeting compliance standards, robust cloud application security is essential for operational success in today’s digital-first world.
 Source: Statista.com
Source: Statista.com
Why Investing in Cloud Application Security Is Important for Businesses
Cloud application security is a foundational element for modern businesses, enabling them to operate securely and efficiently in an increasingly digital world. Here’s why it’s a critical investment:
1. Safeguarding Sensitive Data
Sensitive business and customer information are primary targets for cyberattacks. By implementing cloud application security best practices, businesses can ensure robust encryption, secure access controls, and real-time threat monitoring. These measures protect data integrity and confidentiality, reducing the risk of breaches and unauthorized access.
2. Compliance with Regulations
Adhering to industry-specific regulations like GDPR, HIPAA, and PCI DSS is a critical obligation for businesses. Cloud computing security compliance ensures that security protocols align with regulatory standards, reducing the risk of legal penalties and enhancing trust among stakeholders.
3. Protecting Brand Reputation
Data breaches can severely damage a company’s reputation and customer trust. Application security in cloud computing helps prevent breaches by offering proactive security measures, such as intrusion detection and incident response systems. This fosters customer loyalty and strengthens market credibility.
4. Enabling Business Continuity
Cyberattacks and system failures can disrupt operations and lead to financial losses. By leveraging cloud security technologies, businesses can implement automated recovery systems and redundancy measures to ensure uninterrupted service. This resilience supports seamless operations even during unforeseen incidents.
5. Enhancing Operational Efficiency
Manual security processes can be time-consuming and error prone. Cloud-based application security integrates automated tools for threat detection, compliance monitoring, and access management. This streamlines operations, reduces overhead, and allows IT teams to focus on strategic initiatives.
6. Scaling Securely
As businesses expand, their cloud environments must accommodate increased data, users, and complexity. Security management in cloud computing offers scalable solutions that grow with the organization, ensuring consistent protection as operations evolve. Additionally, cloud security plays a key role in digital transformation services, supporting businesses as they modernize and scale their operations.
7. Cost Savings
Investing in best practices for cloud security proactively mitigates the financial risks associated with breaches, such as recovery costs, legal fees, and lost business. This approach ensures resource efficiency while maintaining robust security measures, ultimately saving money in the long term.
Key Strategies to Secure Cloud Applications
Securing cloud applications involves implementing advanced strategies that safeguard sensitive data, ensure operational efficiency, and maintain compliance. Below are the essential strategies and how they enhance cloud application security:
 Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA)
MFA ensures that access to cloud applications is protected by requiring multiple verification steps, such as passwords, one-time codes, or biometrics. To implement MFA, configure your cloud systems to prompt for at least two forms of verification before granting access.
This can include something the user knows (password), something the user has (mobile device), or something the user has (biometric data). We guide you in integrating cloud application security protocols, including MFA, to significantly reduce the likelihood of data breaches and enhance security compliance.
 Regular Security Audits
Regular Security Audits
Periodic reviews of cloud configurations identify vulnerabilities and misconfigurations that may expose systems to threats. Schedule regular security audits using automated scanning tools and expert reviews to assess vulnerabilities in your cloud infrastructure.
Remediate identified risks promptly to avoid exposure. Our team ensures that your business stays compliant with cloud computing security compliance protocols, conducting thorough audits to identify potential threats and resolve them efficiently.
 Data Encryption
Data Encryption
Encryption ensures that sensitive data remains protected during storage (at rest) and transmission (in transit). Encrypt all sensitive data using AES-256 or similar high-strength encryption standards during storage and transmission across all devices and platforms.
By following cloud data security best practices, we ensure that all your critical information is encrypted and securely stored, preventing unauthorized access and maintaining compliance with industry standards.
 Continuous Monitoring
Continuous Monitoring
Monitoring tools actively track cloud activities, identifying potential security breaches and unusual behaviors in real time. Leverage automated monitoring tools that track every event across your cloud infrastructure.
These tools use machine learning to identify deviations from standard activities and alert administrators to potential threats. By implementing cloud security technologies, we provide real-time monitoring solutions that allow your business to react swiftly to threats, ensuring constant vigilance in your cloud ecosystem.
 Zero-Trust Architecture
Zero-Trust Architecture
Zero-trust approaches enforce strict access control policies, ensuring that no user or device is trusted by default. Implement a zero-trust framework by requiring verification for every access request and continuously monitoring user behavior.
Use micro-segmentation and identity-based policies to limit access based on necessity. We design and deploy custom enterprise solutions that incorporate zero-trust architecture to ensure that access is restricted, and every request is scrutinized, protecting your data from both internal and external threats.
 API Security
API Security
APIs are vital for cloud functionality but can be vulnerable if not secured properly. Implement strong authentication methods like OAuth and enforce rate-limiting and encryption across all API endpoints to prevent unauthorized access and misuse.
Our team uses application security in cloud strategies to ensure your APIs are securely protected, offering seamless integration while preventing data breaches and unauthorized data manipulation.
 Employee Training
Employee Training
Employees are often the weakest link in security. Training ensures they understand and follow best practices for safeguarding cloud applications.Conduct regular training programs to educate employees about secure practices, phishing recognition, password management, and data protection. Provide refresher courses to ensure knowledge retention.
We offer strategic cloud security best practices training tailored to your business, ensuring that employees are well-prepared to handle sensitive information securely, reducing the risk of breaches due to human error.
Discover How Advanced Security Strategies Can Support Your Growth Journey.
Technologies Driving Cloud Application Security
The evolution of cloud application security is heavily driven by advanced technologies that safeguard data, ensure compliance, and mitigate threats. Here’s a detailed look at these transformative technologies and how they contribute to a robust security framework.
Artificial Intelligence (AI)
- AI is a game-changer in security, leveraging machine learning algorithms to analyze large datasets, detect anomalies, and predict potential threats. It continuously adapts to emerging risks, offering proactive threat mitigation.
- AI integration services empower organizations to enhance cloud application security by automating threat detection and delivering real-time insights, minimizing vulnerabilities, and improving response times.
Cloud Access Security Brokers (CASBs)
- CASBs bridge the gap between cloud applications and users, enforcing critical security measures like encryption, compliance tracking, and real-time access controls. They monitor cloud usage patterns and identify unauthorized activities.
- This technology ensures businesses adhere to cloud computing security compliance standards while gaining comprehensive visibility into their cloud environments, safeguarding data from potential breaches.
Secure Web Gateways (SWGs)
- SWGs protect cloud applications by filtering and monitoring web traffic. They block access to malicious websites, prevent phishing attempts, and safeguard users from web-based threats.
- By adopting SWGs, organizations align with cloud security best practices, ensuring safe browsing experiences and reducing risks associated with external threats.
Security Information and Event Management (SIEM) Tools
- SIEM tools collect, process, and analyze security-related data from various sources. They provide centralized dashboards for real-time monitoring, enabling organizations to identify vulnerabilities swiftly.
- SIEM tools enhance security management in cloud computing by offering actionable insights that help IT teams respond to incidents faster and more effectively.
Data Loss Prevention (DLP) Solutions
- DLP tools monitor and protect sensitive information by identifying unauthorized attempts to access, share, or transmit critical data. They enforce encryption policies and restrict data flow to authorized channels.
- DLP solutions ensure adherence to cloud data security best practices, mitigating risks of accidental leaks and enhancing compliance with industry regulations like GDPR and HIPAA.
Identity and Access Management (IAM)
- IAM solutions manage user access by verifying identities through multi-factor authentication (MFA) and role-based permissions. This approach ensures that only authorized users access sensitive applications and data.
- IAM strengthens application security in cloud computing, streamlining access management while reducing the likelihood of unauthorized breaches.
At Matellio, we specialize in integrating cutting-edge technologies into custom security solutions tailored to your business needs. From leveraging AI for proactive threat management to implementing robust IAM and DLP solutions, we ensure your cloud applications remain secure, scalable, and compliant.
Challenges in Cloud Application Security
While cloud application security is essential for protecting sensitive data and ensuring business continuity, it presents distinct challenges that businesses must address proactively. Here’s a detailed exploration of these challenges and effective strategies to overcome them.
Data Breaches
Challenge: Cybercriminals target cloud environments to access sensitive business and customer data. Breaches can result from weak passwords, misconfigured access settings, or vulnerabilities in third-party integrations, leading to severe financial and reputational damage.
Solution: Implement advanced encryption for data at rest and in transit. Utilize cloud application security tools with intrusion detection systems to monitor and protect data from unauthorized access. Regularly audit access logs and enforce strict identity and access management policies.
Compliance Complexity
Challenge: Businesses operating in multiple regions must comply with various regulations, such as GDPR, HIPAA, or PCI DSS, which often have overlapping but distinct requirements. Failing to adhere to these regulations can result in hefty fines and legal issues.
Solution: Collaborate with experts in cloud computing security compliance to automate compliance tracking and implement pre-defined templates for regulatory alignment. Conduct regular audits and utilize compliance dashboards to stay informed about legal obligations.
Misconfigured Security Settings
Challenge: Human errors in configuring security settings, such as public access permissions or weak API controls, can expose critical assets to attackers. These misconfigurations are a leading cause of data breaches in cloud environments.
Solution: Use automated configuration management tools that align with cloud security best practices to detect and remediate misconfigurations in real time. Enable role-based access control (RBAC) to ensure only authorized personnel can modify settings.
Shared Responsibility Model
Challenge: Businesses often misunderstand the shared responsibility model of cloud service providers, leaving critical aspects like application-level security unmanaged, which increases the risk of vulnerabilities.
Solution: Clearly outline security roles and responsibilities in service-level agreements (SLAs). Use application security in cloud computing platforms to manage user-side responsibilities effectively and ensure collaboration between internal teams and cloud providers.
Rapid Scalability
Challenge: As businesses grow, rapid scaling of operations can result in inconsistent security measures, making it easier for attackers to exploit vulnerabilities during expansion.
Solution: Adopt Cloud migration services with scalable security architectures. These services provide automated scaling mechanisms that adjust security measures dynamically to match the size and scope of operations while maintaining robust protection.
Insider Threats
Challenge: Malicious or negligent actions by employees or contractors can lead to security breaches, data loss, or intentional sabotage.
Solution: Implement strict role-based access controls and continuous monitoring using security management in cloud computing systems. Regular employee training should be conducted to raise awareness of security protocols and recognize potential threats early.
Integration Challenges
Challenge: Integrating cloud applications with on-premises systems or other cloud services increases the risk of data leakage and inconsistent security protocols.
Solution: Use secure APIs and middleware with built-in cloud security technologies to enable seamless and safe communication between systems. Conduct integration testing to ensure data remains secure throughout the process.
Continuous Threat Evolution
Challenge: The dynamic nature of cyber threats, including zero-day vulnerabilities and advanced persistent threats (APTs), requires constant vigilance and updates to security frameworks.
Solution: Deploy AI-powered threat detection systems through integration services to identify anomalies and respond to potential threats proactively. Regularly update security software and conduct threat simulation exercises to ensure preparedness.
Cost Constraints
Challenge: Small and medium-sized businesses often struggle to allocate sufficient budgets for advanced cloud security measures, leaving them vulnerable to attacks.
Solution: Invest in cost-effective cloud-based application security solutions that scale with business needs. Leverage pay-as-you-go models for advanced tools, ensuring affordability without compromising security.
Shadow IT
Challenge: Employees often use unauthorized cloud applications, leading to unmonitored and unsecured data transfers. This practice, known as shadow IT, increases the risk of breaches.
Solution: Implement centralized monitoring solutions and enforce policies through cloud application security best practices to identify and manage unauthorized applications. Educate employees on the importance of using approved tools and systems.
Discover How Tailored Cloud Solutions Can Keep Your Applications Secure And Future-Ready!
Future Trends in Cloud Application Security
As businesses increasingly rely on cloud infrastructure, the need for adaptive and advanced security solutions has never been greater. Emerging trends in cloud application security reflect the dynamic nature of threats and the innovative responses required to mitigate them. These trends are reshaping the way organizations protect sensitive data, ensure compliance, and maintain operational continuity.
AI-Driven Security
- Artificial Intelligence (AI) has emerged as a transformative force in cloud security, enabling predictive and responsive solutions.
- AI systems analyze large datasets to detect anomalies, predict attack patterns, and automate responses in real-time. This includes identifying previously unknown threats through machine learning.
- By integrating AI development services, businesses can proactively defend against sophisticated cyberattacks. AI-driven systems reduce the workload on security teams, enhancing efficiency and accuracy in threat mitigation.
Zero-Trust Architectures
- The traditional perimeter-based security model is giving way to zero-trust frameworks, which prioritize verification over implicit trust.
- Zero-trust involves continuous verification of users and devices, multi-factor authentication (MFA), and role-based access controls. It enforces strict policies for accessing sensitive resources, regardless of location.
- This approach strengthens cloud technology security by ensuring that only authorized users and devices can access critical systems, effectively minimizing insider threats and unauthorized access.
Secure DevOps (DevSecOps)
- The integration of security into the DevOps process is redefining how secure applications are developed and deployed.
- DevSecOps automates security testing during development, includes vulnerability scanning in CI/CD pipelines, and ensures real-time monitoring post-deployment.
- Embedding cloud security best practices early in the development lifecycle reduces the risk of vulnerabilities in live environments, saving time and resources while ensuring robust application security.
Cloud-Native Security Platforms
- Designed specifically for the cloud, these platforms offer comprehensive solutions that address modern multi-cloud complexities.
- Cloud-native platforms integrate features like encryption, identity management, and threat analytics into a unified dashboard. These solutions are optimized for hybrid and multi-cloud infrastructures.
- By adopting cloud-based application security, businesses gain operational visibility and streamlined security management, which is essential for large-scale, distributed operations.
- Endpoint Security Integration
- The proliferation of remote work and IoT devices has elevated the importance of endpoint security.
- Endpoint security tools continuously monitor devices for compliance, isolate compromised endpoints, and enforce security policies. This includes encryption and real-time malware detection.
- Securing endpoints ensures that devices accessing cloud application security environments do not introduce vulnerabilities, supporting secure remote work and BYOD policies.
Automation in Threat Mitigation
- Automation is rapidly becoming a cornerstone of modern security strategies, reducing the reliance on manual interventions.
- Automated systems detect and neutralize threats in real-time by leveraging machine learning and pre-defined rules. Alerts are generated for further investigation, allowing security teams to focus on high-priority issues.
- Automation enhances efficiency and supports security management in cloud computing, enabling businesses to maintain uninterrupted operations even during attacks.
Advanced-Data Governance
- Data governance is crucial for maintaining control over how data is handled, stored, and accessed in the cloud.
- Governance tools automate compliance checks, enforce data handling policies, and provide visibility into data flows across systems. Regular audits ensure adherence to standards like GDPR and HIPAA.
- With cloud computing security compliance, businesses avoid regulatory penalties, safeguard sensitive information, and maintain customer trust by demonstrating accountability.
Unified Security Through Cloud Integration
- Seamless integration between various cloud platforms and on-premises systems is vital for security and operational efficiency.
- Cloud integration services facilitate secure data exchange, consistent application of security policies, and unified monitoring across hybrid environments.
- Effective integration reduces redundancies, streamlines workflows, and enhances cloud application security, ensuring a cohesive and secure infrastructure.
Reach Out to Explore How Zero-Trust Architecture Can Protect Your Business.
How Can Matellio Help with Cloud Application Security?
In an era of ever-evolving cyber threats, robust cloud application security is crucial for safeguarding sensitive data, ensuring compliance, and maintaining operational resilience. Advanced cloud security measures enable businesses to mitigate risks, streamline operations, and build trust with customers.
Why Choose Matellio?
At Matellio, we specialize in delivering tailored cloud application security solutions designed to align with your unique business requirements. Whether you need advanced threat detection, secure data management, or compliance assurance, our team develops scalable and resilient security frameworks to protect your cloud infrastructure.
- We conduct in-depth evaluations of your existing cloud environment, identifying vulnerabilities and potential risks. By leveraging cloud security technologies, we design actionable strategies to enhance your application security.
- Our team implements multi-layered security frameworks, including cloud technology security, zero-trust architectures, and advanced firewalls. This ensures a robust defense against both external and internal threats.
- We develop and implement security measures aligned with industry standards like GDPR, HIPAA, and PCI DSS. Our cloud computing security compliance services ensure your organization avoids penalties while maintaining a trusted reputation.
- Leveraging cutting-edge tools like AI-driven threat detection and SIEM platforms, we enable businesses to identify and mitigate risks in real-time. This proactive approach ensures your applications remain resilient against advanced cyberattacks.
- Our solutions include end-to-end encryption for data at rest and in transit, combined with strong access controls like multi-factor authentication. This protects sensitive information from breaches while ensuring secure access.
- We ensure that your cloud applications integrate seamlessly with existing tools such as CRMs, ERP platforms, and IoT devices. This creates a unified security ecosystem, streamlining workflows and reducing vulnerabilities.
- Our experts provide continuous monitoring, regular updates, and performance optimizations to keep your cloud environment secure and future ready. Using security management in cloud computing, we adapt your security posture to evolving threats.
- Our security frameworks are designed to scale with your business, ensuring protection as you expand operations. Whether you’re adopting application security or implementing hybrid solutions, we ensure robust protection while leveraging our technology consulting services to guide you toward the most efficient and effective strategies.
By partnering with Matellio, you gain access to a team of experts dedicated to safeguarding your cloud applications. Fill out the form today to connect with our specialists and explore how our cloud application security solutions can empower your business with resilient and scalable protection.
Cloud Application Security Services – FAQ’s:
Q1. What makes Matellio’s cloud application security services unique?
We combine advanced tools, compliance-driven strategies, and personalized security frameworks to deliver comprehensive protection tailored to your needs.
Q2. How does Matellio ensure compliance with cloud security regulations?
We implement solutions aligned with global standards, including GDPR, HIPAA, and PCI DSS. Regular audits and secure protocols ensure ongoing compliance.
Q3. Can Matellio secure hybrid or multi-cloud environments?
Yes, we provide security solutions for hybrid and multi-cloud setups, ensuring seamless integration and protection across diverse platforms.
Q4. What is the cost of cloud application security services?
The cost depends on your infrastructure's complexity and specific security needs. We offer transparent and customized pricing to fit your budget.
Q5. How does Matellio handle real-time threat detection?
We use AI and machine learning-driven tools to detect anomalies and respond to threats proactively, ensuring uninterrupted operations.
Q6. Does Matellio offer post-deployment security support?
Yes, we provide continuous monitoring, updates, and optimization to keep your cloud applications secure and aligned with emerging threats.
Q7. How long does it take to implement cloud application security measures?
Timelines vary based on the scope of the project. Our structured approach ensures efficient and timely implementation without disrupting operations.
 Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) Regular Security Audits
Regular Security Audits Data Encryption
Data Encryption Continuous Monitoring
Continuous Monitoring Zero-Trust Architecture
Zero-Trust Architecture API Security
API Security Employee Training
Employee Training


