
The integration of biometrics has revolutionized modern security and convenience. Among these, face recognition technology stands out as a game-changer, enabling seamless identification, enhanced security, and improved user experiences. Its growing applications in various industries highlight its potential as a powerful tool for authentication and personalization.
Businesses investing in face recognition app development not only meet the demands of tech-savvy users but also position themselves as pioneers in leveraging advanced technologies for competitive advantage.
What Is Face Recognition Technology?
Face recognition technology identifies and verifies individuals by analyzing their facial features. It employs a combination of image processing, artificial intelligence (AI), and machine learning algorithms to deliver accurate results.
Key components include:
- Face Detection: Locating faces within images or videos.
- Feature Extraction: Identifying unique facial landmarks like the distance between eyes or the shape of the jawline.
- Matching: Comparing extracted features against a database for verification.
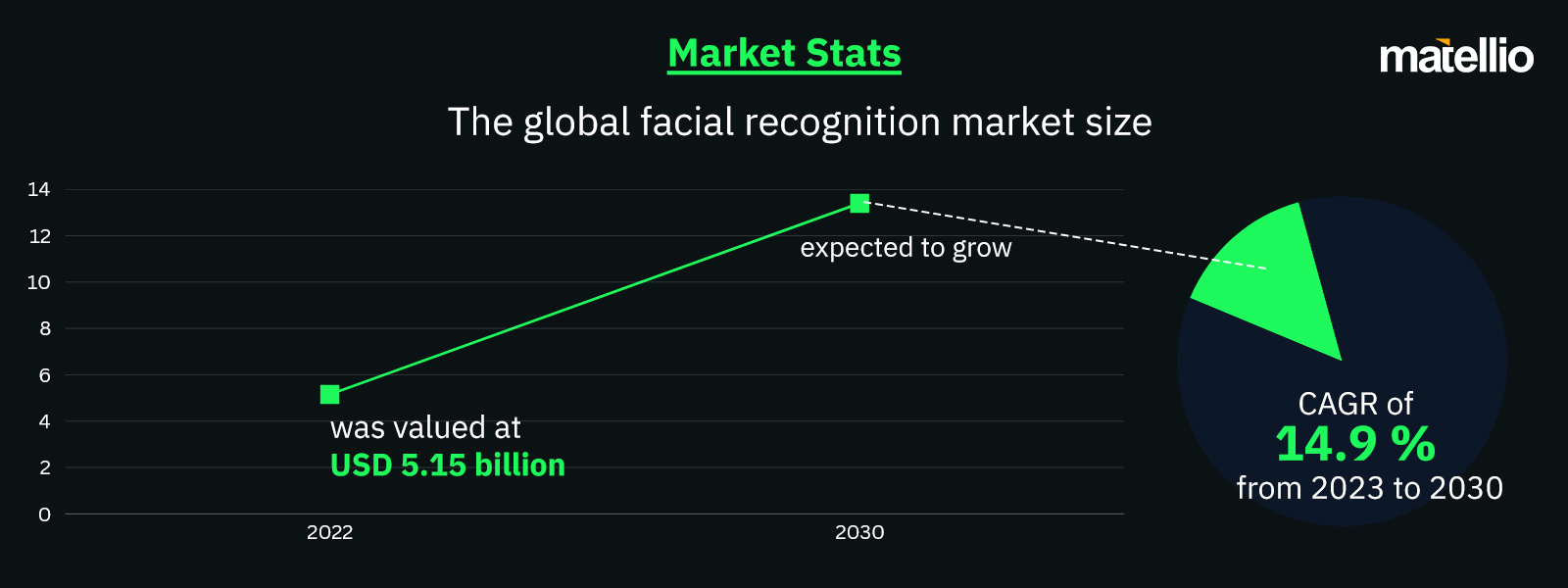
Source – Grand View Research
Why Invest in Face Recognition App Development?
Face recognition technology has transformed how businesses approach security, authentication, and user engagement. By offering advanced features and seamless interactions, face recognition apps are rapidly becoming essential tools across industries. Investing in face recognition app development enables businesses to enhance operational workflows, deliver personalized experiences, and build robust security systems, making it a strategic move for those seeking innovation and operational excellence.
Below, we explore the reasons why businesses should prioritize this technology and how it can drive growth and success.
 Enhanced Security
Enhanced Security
Security remains a top priority for businesses handling sensitive data or operations. Unlike traditional authentication systems that rely on passwords, which can be stolen or guessed, apps that use biometrics provide unparalleled security. A photo app with face recognition goes beyond simple identity verification by ensuring users are authenticated based on unique biological markers.
For example, integrating face recognition technology into enterprise systems ensures that only authorized personnel can access sensitive data or facilities. This advanced layer of security reduces the risks of identity theft and fraud, protecting businesses and their customers alike.
 User Convenience
User Convenience
Face recognition eliminates the need for manual inputs like typing passwords or using physical IDs. Users can unlock devices, authorize payments, or access services with a simple scan, making the process swift and effortless. An iPhone app for face recognition exemplifies this convenience by allowing users to unlock their devices instantly or make secure transactions seamlessly.
This contactless approach is particularly beneficial in environments where hygiene and speed are critical, such as healthcare or retail. By simplifying user interactions, businesses enhance customer satisfaction while reducing friction points in daily operations.
 Operational Efficiency
Operational Efficiency
Automating identification processes with apps equipped with face recognition capabilities significantly improves operational workflows. Tasks like attendance tracking, visitor management, and customer onboarding, which previously required manual intervention, are now automated with precision.
For instance, a face recognition app for Android can be used in workplaces to log employee check-ins and check-outs automatically, reducing the need for manual records. Similarly, customer verification in banks can be streamlined, saving time for both staff and customers. This automation allows businesses to focus on strategic initiatives while maintaining accuracy and efficiency.
 Personalized User Experience
Personalized User Experience
Personalization is a game-changer in customer engagement, and apps with face recognition capabilities make it possible to deliver highly tailored experiences. By identifying users and analyzing their preferences, businesses can provide recommendations or services that resonate with individual needs.
For instance, a face shape recognition app in the beauty or fashion industry can suggest products that complement the user’s facial structure, enhancing the shopping experience. Similarly, in hospitality, an app could pre-load guest preferences based on previous visits, ensuring a memorable and customized service.
 Scalability
Scalability
Face recognition technology is inherently scalable, making it suitable for businesses of all sizes and industries. Starting with basic use cases like employee attendance, businesses can expand to advanced applications, such as customer verification or security enhancements.
Cloud-based solutions further enhance scalability, allowing businesses to accommodate growing user demands without compromising app performance. A digital transformation services approach ensures that face recognition apps are built to adapt to future needs, enabling businesses to stay competitive in a rapidly evolving market.
 Multi-Platform Compatibility
Multi-Platform Compatibility
One of the key advantages of face recognition technology is its compatibility with multiple platforms, ensuring seamless performance across devices. Whether it’s a face recognition app for an iPhone or an Android device, businesses can reach a broader audience and provide consistent functionality.
This cross-platform approach is especially beneficial for enterprises catering to diverse user bases, as it ensures accessibility and uniformity, regardless of the device or operating system being used. Apps built with this flexibility attract tech-savvy customers and meet the demands of modern users.
 Competitive Edge
Competitive Edge
Adopting advanced technologies like face recognition positions businesses as forward-thinking and innovative leaders in their industries. A well-designed AI face recognition app not only enhances user experiences but also sets a company apart from competitors relying on outdated systems.
For example, financial institutions using apps that incorporate real-time facial authentication gain customer trust by demonstrating a commitment to security. Similarly, retail stores offering personalized shopping experiences through apps that use face recognition can attract and retain more customers, building long-term loyalty.
Essential Features of a Face Recognition App
A face recognition app’s effectiveness depends on its features. From fundamental functionalities to next-gen innovations, these features ensure the app meets both user expectations and business requirements.
| Core Features | Next-Gen Features |
| Real-time face detection | AI-driven emotion analysis |
| Multi-platform compatibility | Adaptive learning for user behavior |
| Data encryption for security | Integration with wearable devices |
| Integration with existing systems | Predictive analytics for user trends |
| User-friendly interface | Advanced liveness detection |
Industries Leveraging Face Recognition Apps
Face recognition technology is revolutionizing industries by enhancing security, operational efficiency, and user experiences. With real-time authentication and precise identification, this technology serves diverse industry needs. Below, we explore how various industries utilize face recognition app development and related innovations.
 Healthcare
Healthcare
In healthcare, precision is essential. Apps with face recognition capabilities ensure accurate patient identification, reducing errors and improving efficiency. For example, face recognition technology can streamline patient check-ins, enabling quick access to electronic health records. Coupled with RPA services, healthcare providers can automate workflows like appointment scheduling and billing, further enhancing operational efficiency and patient satisfaction.
 Retail
Retail
Retailers leverage apps that use face recognition to enhance in-store experiences and improve security. These apps identify loyal customers, enabling personalized recommendations based on shopping history. Simultaneously, they act as a deterrent against shoplifting by recognizing known offenders. This dual-purpose technology helps retailers build stronger customer relationships while protecting assets.
 Finance
Finance
Security breaches are a major concern in the financial industry. An AI face recognition app enhances fraud prevention by offering secure biometric authentication for transactions. This eliminates the risks associated with traditional methods like passwords or PINs. Additionally, face recognition technology ensures faster and safer verification processes, building customer trust and ensuring compliance with strict financial regulations.
 Education
Education
Educational institutions benefit significantly from these apps. It simplifies attendance tracking, allowing students to check in digitally, which saves time and ensures accuracy. They also enhance campus security by controlling access to facilities. Incorporating cross-platform app development ensures these apps function seamlessly across devices, including desktops, tablets, and smartphones, offering consistent and reliable performance.
 Public Sector
Public Sector
The public sector extensively uses face recognition photo apps for surveillance and public safety. Law enforcement agencies leverage this technology to monitor public areas, identify individuals on watchlists, and improve urban security. For instance, at airports, face recognition systems streamline passenger identification, reducing wait times and bolstering security. Governments adopting this technology can ensure efficient management of public safety.
 Hospitality
Hospitality
Hotels and resorts integrate the iPhone app for face recognition to deliver exceptional guest experiences. By recognizing guests upon arrival, staff can provide personalized services, such as pre-arranged room settings or exclusive activity recommendations. Additionally, this technology ensures property security by restricting access to private areas, such as VIP lounges or guest suites, offering peace of mind alongside luxury.
 Manufacturing and Logistics
Manufacturing and Logistics
In manufacturing, managing large teams and ensuring secure access to facilities is crucial. Face recognition for the Android app streamlines attendance tracking, eliminating manual logs and reducing errors. When combined with facial recognition, logistics companies can verify drivers and secure warehouse access, improving operational workflows and minimizing risks. By leveraging these features, businesses can maintain security and boost productivity.
Elevate Your Customer Experience with a Next-Generation Face Recognition App! Developing a face recognition app involves a well-structured approach that combines technical expertise with strategic planning. Each stage plays a critical role in ensuring the app’s functionality, security, and user-friendliness. Below is an elaborate guide to creating a successful face recognition app: Monetizing a face recognition app is essential for ensuring long-term profitability while delivering value to users. The right strategy not only generates revenue but also enhances the app’s usability and appeal. Below is a detailed exploration of effective monetization strategies: The freemium model offers basic app functionality for free while charging for advanced or premium features. This strategy attracts a wide user base and encourages users to upgrade to paid plans once they recognize the app’s value. A photo app with face recognition might allow users to organize photos and detect faces for free, while premium features such as unlimited photo storage or high-resolution downloads are offered at a subscription fee. Why It Works: A subscription model involves charging users a recurring fee (monthly, quarterly, or annually) to access premium features. Tiered pricing options allow users to choose a plan based on their needs and budget. A face recognition app iPhone for photographers could offer a basic plan for photo organization and a premium plan for advanced editing tools and facial recognition analytics. Why It Works: The pay-per-use model charges users for specific services or features each time they use them. This approach is ideal for businesses or individuals who require occasional access to the app’s capabilities. An app with face recognition designed for security purposes might charge businesses on a per-scan basis for verifying employee identities. Why It Works: Partnering with brands to display ads within the app is a common way to generate revenue without charging users directly. Ads can be tailored to user interests, increasing relevance and engagement. A face recognition app Android used by casual users might display ads for camera accessories or related apps during non-intrusive moments, such as loading screens. Why It Works: Aggregated and anonymized data collected through the app can be monetized by selling insights to research organizations, marketing firms, or industry partners. Adhering to privacy regulations like GDPR and CCPA is critical to this strategy. A face shape recognition app in the beauty industry could license anonymized data to cosmetics companies for market research and product development insights. Why It Works: Offering enterprise licensing allows businesses to use the app’s capabilities on a larger scale. This strategy involves charging a flat fee or subscription for access to the app’s features tailored to enterprise needs. A security-focused app using Azure integration services could be licensed to enterprises, enabling them to integrate the app into their existing systems for employee verification or visitor management. Why It Works: Offering custom development services allows businesses to tailor the app to their unique requirements. This approach involves charging for customization, integration, or additional feature development. Enterprises looking to hire dedicated developers could work with the app’s development team to add industry-specific features or integrate the app with existing systems. Why It Works: Ready to Build a Secure, Scalable, and Engaging Face Recognition App? Developing a custom app is a highly complex task involving numerous challenges that impact functionality, performance, and user experience. Tackling these challenges effectively ensures the app is secure, scalable, and user-friendly. Below is an in-depth exploration of the major challenges in face recognition app development, along with solutions. One of the critical challenges in face recognition is achieving consistent accuracy in varied environmental conditions. Factors like lighting, camera angles, facial expressions, and background interference can significantly affect the app’s performance, especially in uncontrolled environments. To overcome this, the app must incorporate robust machine learning models trained on diverse datasets representing various lighting and positional scenarios. This approach ensures the app adapts to different conditions effectively. Additionally, apps can utilize IoT deployment services to connect with advanced cameras and sensors, enhancing accuracy in capturing and recognizing facial features under challenging environments. Face recognition apps often handle sensitive biometric data, raising privacy concerns among users. Protecting this data from breaches and ensuring compliance with data privacy regulations like GDPR and CCPA is critical to maintaining user trust. Implementing strong encryption mechanisms and secure data handling practices is essential for safeguarding user data. Processing data locally on devices, such as through a face recognition app on Android, minimizes the risk of unauthorized access by reducing dependence on external servers. Transparent communication about data usage also helps build user confidence in the app’s security. Fast and reliable processing is crucial for face recognition apps, particularly those requiring real-time recognition, such as security or retail applications. Any delay in recognition can hinder the app’s usability and effectiveness. To ensure quick response times, developers can optimize algorithms and utilize cloud integration services to enhance processing capabilities. Cloud-based infrastructures allow computationally heavy tasks, such as large-scale facial recognition, to be offloaded, ensuring faster results without straining device resources. This hybrid approach combines speed with reliability for both small and large-scale applications. Ensuring smooth functionality across various devices and operating systems is a significant hurdle. Differences in hardware capabilities, screen sizes, and camera resolutions can affect the app’s performance. A cross-platform approach ensures consistent performance. For instance, a face recognition app iPhone must leverage Apple’s advanced camera and processing technologies, while Android apps need to be optimized for the diverse range of Android devices. Regular testing across multiple devices ensures compatibility and enhances user experience regardless of the platform. Spoofing attacks, where static images or videos are used to mimic legitimate users, pose a serious security risk for face recognition apps. Without adequate safeguards, the app’s reliability and user trust are compromised. Advanced liveness detection techniques, such as analyzing micro-expressions or 3D facial mapping, enhance the app’s ability to differentiate between live faces and fake attempts. This is especially critical for apps that use face recognition in sensitive areas like financial transactions or identity verification. By integrating these measures, the app ensures high security and resilience against spoofing attempts. As the app’s user base grows, it must handle increased volumes of data and user requests without compromising performance. Poor scalability can lead to slow processing times and degraded user experience. A scalable architecture ensures the app performs well under heavy loads. Cloud-based solutions, supported by face recognition photo app systems, enable dynamic resource allocation to manage fluctuating demands. Efficient database management and optimized query handling further improve scalability, allowing the app to grow alongside user needs seamlessly. An intuitive and easy-to-navigate interface is critical for user adoption. Overcomplicated designs or cumbersome workflows can frustrate users and reduce engagement. The app’s design should prioritize simplicity and functionality. For example, a photo app with face recognition should feature straightforward workflows for uploading images and managing recognition tasks. Incorporating user feedback during the design phase ensures the interface aligns with user expectations, enhancing overall satisfaction. Face recognition apps often need to integrate with other systems, such as CRMs, payment gateways, or IoT devices, to offer a comprehensive solution. Ensuring seamless integration while maintaining security is a complex task. Leveraging APIs and middleware ensures smooth integration with third-party systems. For instance, an AI face recognition app designed for enterprise use can connect with IoT-enabled security systems to streamline access control. Secure APIs and compliance with industry standards ensure data exchange between systems is safe and reliable. Face recognition technology is evolving rapidly, driven by innovative applications and cutting-edge advancements. These developments are expanding its utility across industries, making it an indispensable tool for businesses. Below, we explore the key trends: Keep Your Business Future-Ready with Insights into Face Recognition App Trends! In today’s rapidly advancing digital world, face recognition technology is transforming industries by enhancing security, improving user experiences, and streamlining operations. A custom-built face recognition app can empower your business with advanced capabilities such as secure authentication, real-time recognition, and personalized interactions, unlocking new opportunities for growth and efficiency. If you’re considering investing in a face recognition app development, then we offer tailored solutions to meet your unique requirements. Whether it’s for security, healthcare, retail, or other industries, our team of experts delivers robust, scalable, and intuitive apps that ensure a seamless user experience. If you’re ready to revolutionize your operations with a custom face recognition app, Matellio’s expert team is here to help. Fill out the form today to schedule a consultation and begin your journey toward innovation! Building a face recognition app involves understanding user needs, designing intuitive interfaces, developing robust algorithms, integrating real-time facial recognition, and rigorous testing. Matellio can guide you through each step, ensuring a secure and efficient app. Yes, we enable seamless integration with platforms such as IoT devices, CRM systems, and cloud services, expanding the app's capabilities and ensuring smooth operations across systems. Key features include real-time recognition, anti-spoofing measures, liveness detection, multi-factor authentication, and user management tools. We customize these features to align with your business needs. The timeline varies based on the app's complexity and features. After assessing your requirements, we will provide a detailed roadmap to ensure timely delivery. Costs depend on the app's features, design complexity, and platform compatibility. Matellio offers flexible pricing models to deliver a high-quality app within your budget. Step-by-Step Guide to Developing a Face Recognition App
1. Market Research and Ideation
2. Choose the Right Tech Stack
3. Design the User Interface (UI/UX)
4. Develop the Backend and API Integrations
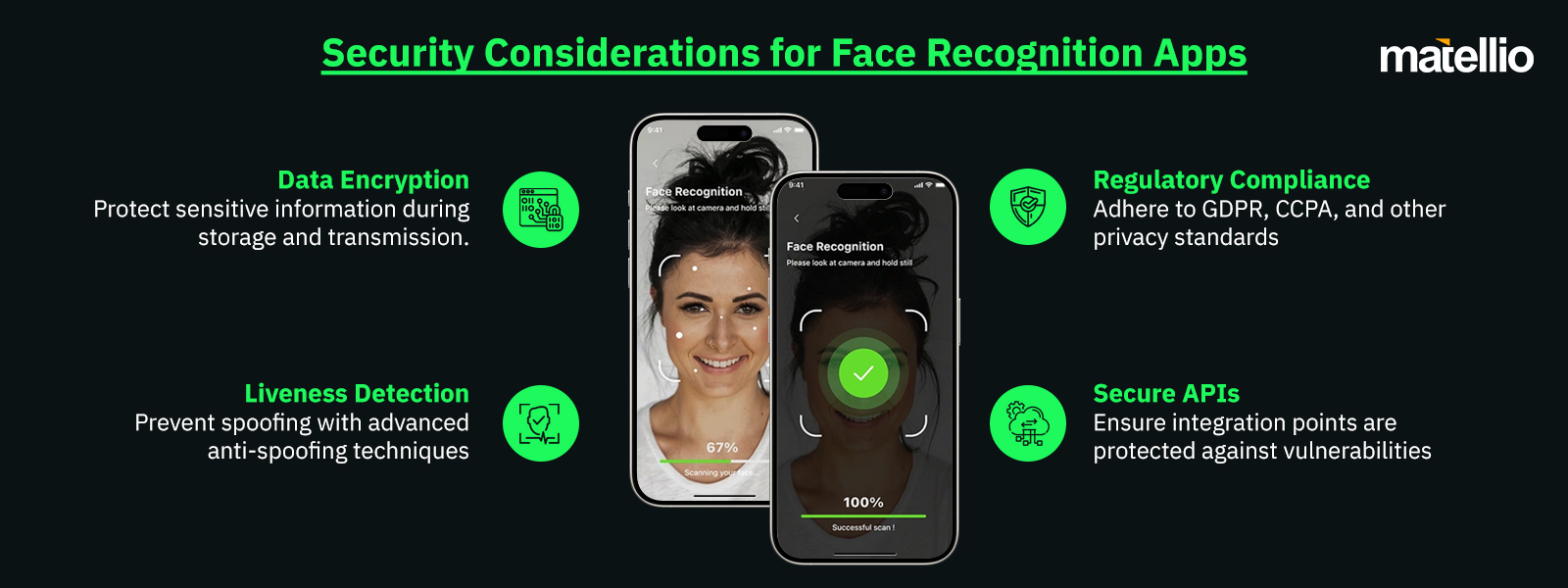
5. Implement Security Protocols
6. Payment Gateway Integration
7. Conduct Testing and Quality Assurance
8. Launch and Gather Feedback
Monetization Strategies for Face Recognition Apps
Freemium Model
Subscription Plans
Pay-Per-Use
In-App Advertising
Data Licensing
Enterprise Licensing
Custom Development and Integration
Challenges in Custom Face Recognition App Development
Accuracy in Diverse Conditions
Challenge:
Solution:
Data Privacy Concerns
Challenge:
Solution:
Processing Speed
Challenge:
Solution:
Device Compatibility
Challenge:
Solution:
Preventing Spoofing
Challenge:
Solution:
Scalability and Performance
Challenge:
Solution:
User Experience and UI Challenges
Challenge:
Solution:
Security Integration with Other Technologies
Challenge:
Solution:
Future Trends in Custom Face Recognition App Development
3D Face Recognition
Integration with IoT Devices
Real-Time Emotion Analysis
Edge Computing
Voice and Face Hybrid Authentication
Advanced Personalization Through AI
How Can Matellio Help You Develop a Face Recognition App?
Here’s How Matellio Can Help Your Business:
Face Recognition App Development FAQ’s
Q1. How to build a face recognition app?
Q2. Can a face recognition app integrate with other platforms?
Q3. What features are essential in a face recognition app?
Q4. What is the timeline for developing a face recognition app?
Q5. How much does face recognition app development cost?
 Enhanced Security
Enhanced Security Operational Efficiency
Operational Efficiency Personalized User Experience
Personalized User Experience Scalability
Scalability Multi-Platform Compatibility
Multi-Platform Compatibility Competitive Edge
Competitive Edge Healthcare
Healthcare Retail
Retail Finance
Finance Education
Education Public Sector
Public Sector Hospitality
Hospitality Manufacturing and Logistics
Manufacturing and Logistics

